-
Analysis of the dovecat and hy4 Linux Malware 27 Oct 2020
A few days ago, a case came in which had some rather odd symptoms, such as processes using high amounts of CPU and memory, and running from the
/tmpdirectory.After asking for some logs, and some samples of the binaries, it became obvious that the system was compromised, and was now running some interesting malware.
In this post, we are going to look into the malware called dovecat, which turned out to be a cryptominer, and hy4, which is a IRC botnet malware dropper.
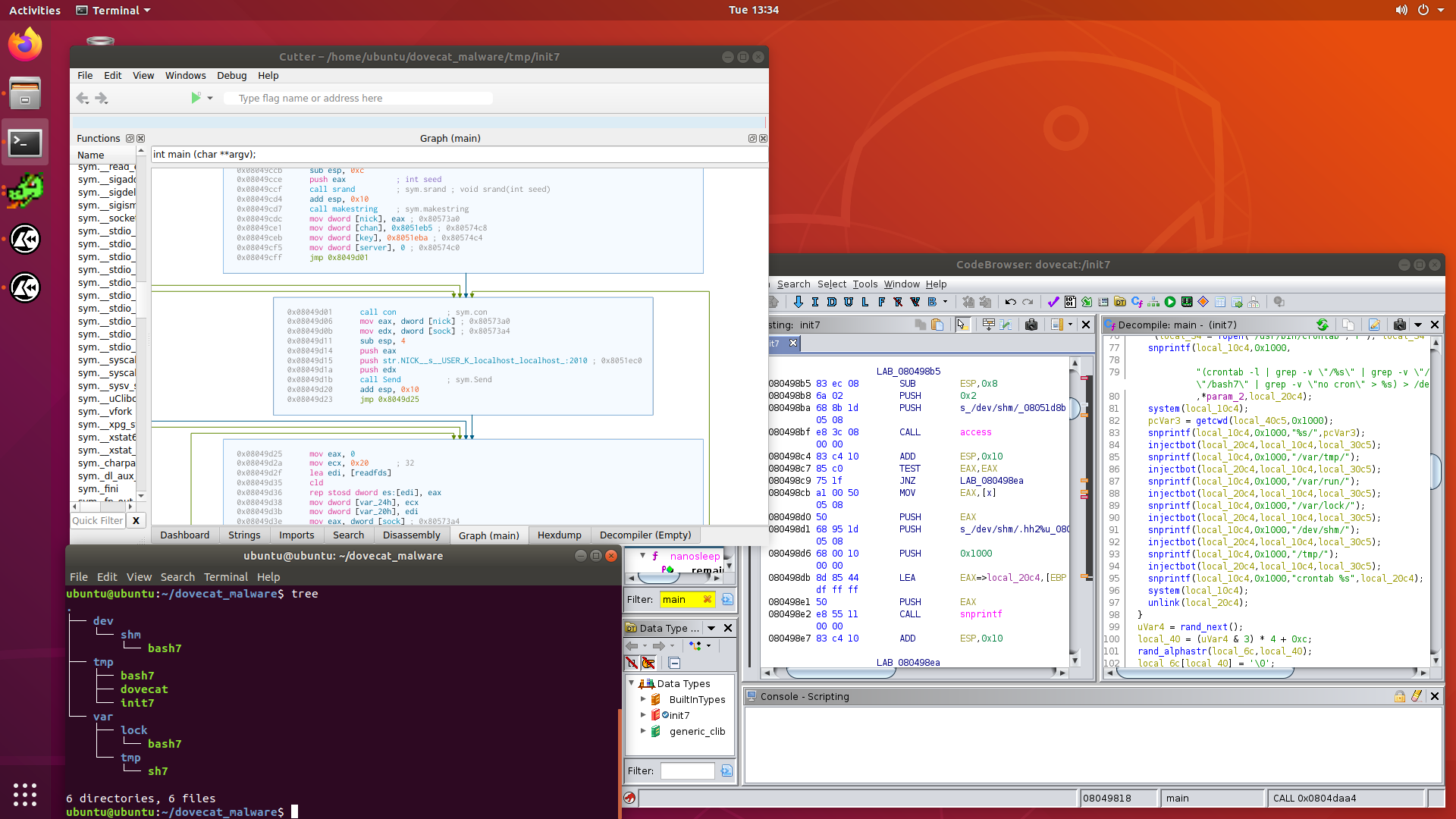
I’m pretty excited, as I haven’t analysed any Linux malware before, and this is real life stuff pulled directly from a production machine, so it still has its fangs intact.
Let’s get started.
-
Crypto Deja vu in TimeLock 1.7 Vulnerability Writeup 07 Apr 2019
Here we are, back for more TimeLock excitement. Let’s see what’s in store for this article, where we pull apart and attempt to find vulnerabilities in TimeLock 1.7.
A little while ago u/cryptocomicon posted a new announcement of TimeLock 1.7 to Reddit:

Looks like I’m getting some advertising of my blog =) Thanks u/cryptocomicon! Maybe it will introduce some people to reverse engineering.
Challenges are fun, so let’s jump into it.
-
Double Trouble With Symmetric Encryption in TimeLock 1.5 Vulnerability Writeup 20 Mar 2019
All right, I hope you liked the previous articles on TimeLock, because here is another one! This will be my fourth bug bounty now. As always, interesting reverse engineering followed by an awesome Bitcoin reward awaits!
A little while ago u/cryptocomicon posted a new announcement of TimeLock 1.5 to Reddit:

I can’t turn down a good challenge, so lets get started!
-
Unleashing a Sybil Attack Against TimeLock 1.3 Vulnerability Writeup 18 Feb 2019
Here we are, back again for my third bug bounty! It really is a good time trying to break an applications security, and especially so when there is some Bitcoin waiting as a reward.
As always, I was on Reddit and saw that u/cryptocomicon has made some changes to TimeLock, and is ready for them to be tested again.
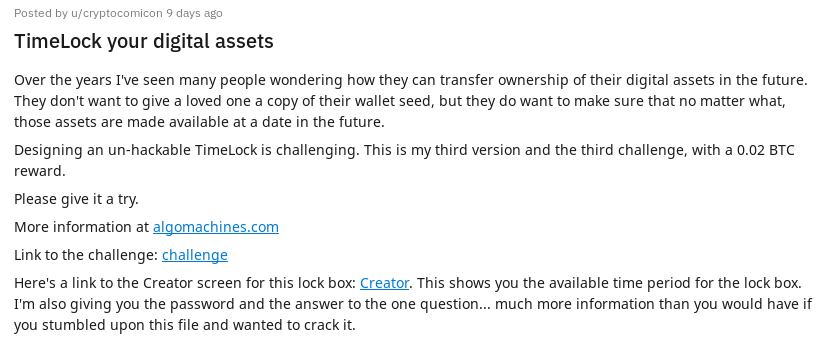
u/cryptocomicon has acknowledged that writing secure software is extremely hard, and is absolutely correct in that statement. We also see that a new challenge is issued:
Designing an un-hackable TimeLock is challenging. This is my third version and the third challenge, with a 0.02 BTC reward.
Please give it a try.
Will do. Challenge accepted.
-
Revisiting TimeLock 1.2 and Vulnerability Writeup 28 Jan 2019
I’m back again for my second bug bounty! Searching for bugs is actually pretty fun, especially when it comes with a generous reward in my favourite cryptocurrency, Bitcoin!
I was scrolling Reddit like usual, and u/cryptocomicon has returned with a new version of TimeLock! That’s great news.
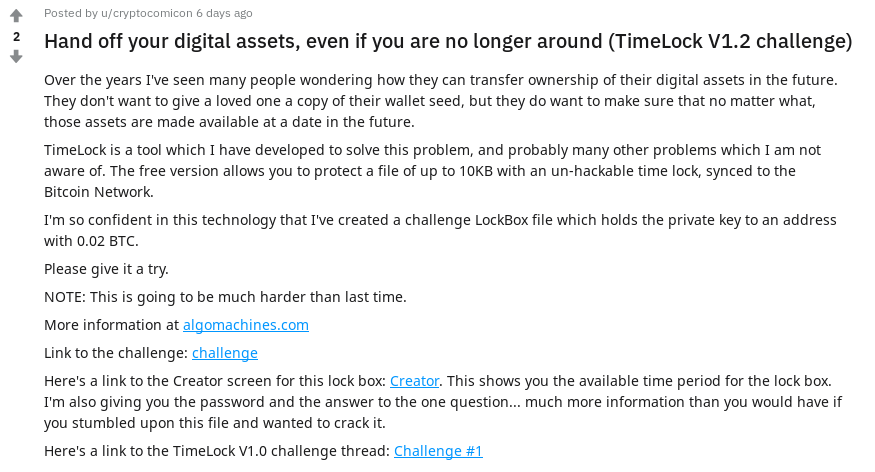
If we remember back to last week, I solved the original TimeLock challenge, and wrote a detailed writeup.
u/cryptocomicon issued a new challenge:
I’m so confident in this technology that I’ve created a challenge LockBox file which holds the private key to an address with 0.02 BTC.
Please give it a try.
NOTE: This is going to be much harder than last time.
Much harder than last time? Sounds interesting.
Challenge accepted.
-
Analysis of TimeLock and Vulnerability Writeup 18 Jan 2019
I have something exciting to share today, my first bug bounty! Hopefully the start of something great. It even came with a generous reward, in my favourite crypto currency, Bitcoin.
I was browsing Reddit as you do, and came across this post on r/bitcoin.
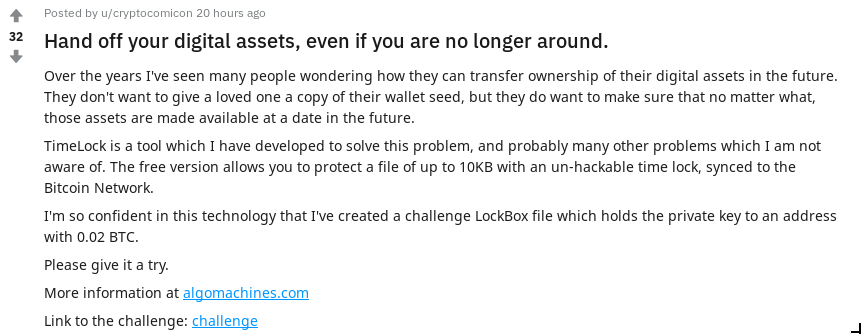
u/cryptocomicon has developed some encryption software which can be used to safely store secrets and release them to the world sometime in the future. The software can encrypt and store arbitrary files, and release them to trusted third parties when you are no longer around. Sounds good for passing on crypto currency wallets and passwords.
u/cryptocomicon issued a challenge:
“I’m so confident in this technology that I’ve created a challenge LockBox file which holds the private key to an address with 0.02 BTC.
Please give it a try.”
Challenge accepted.