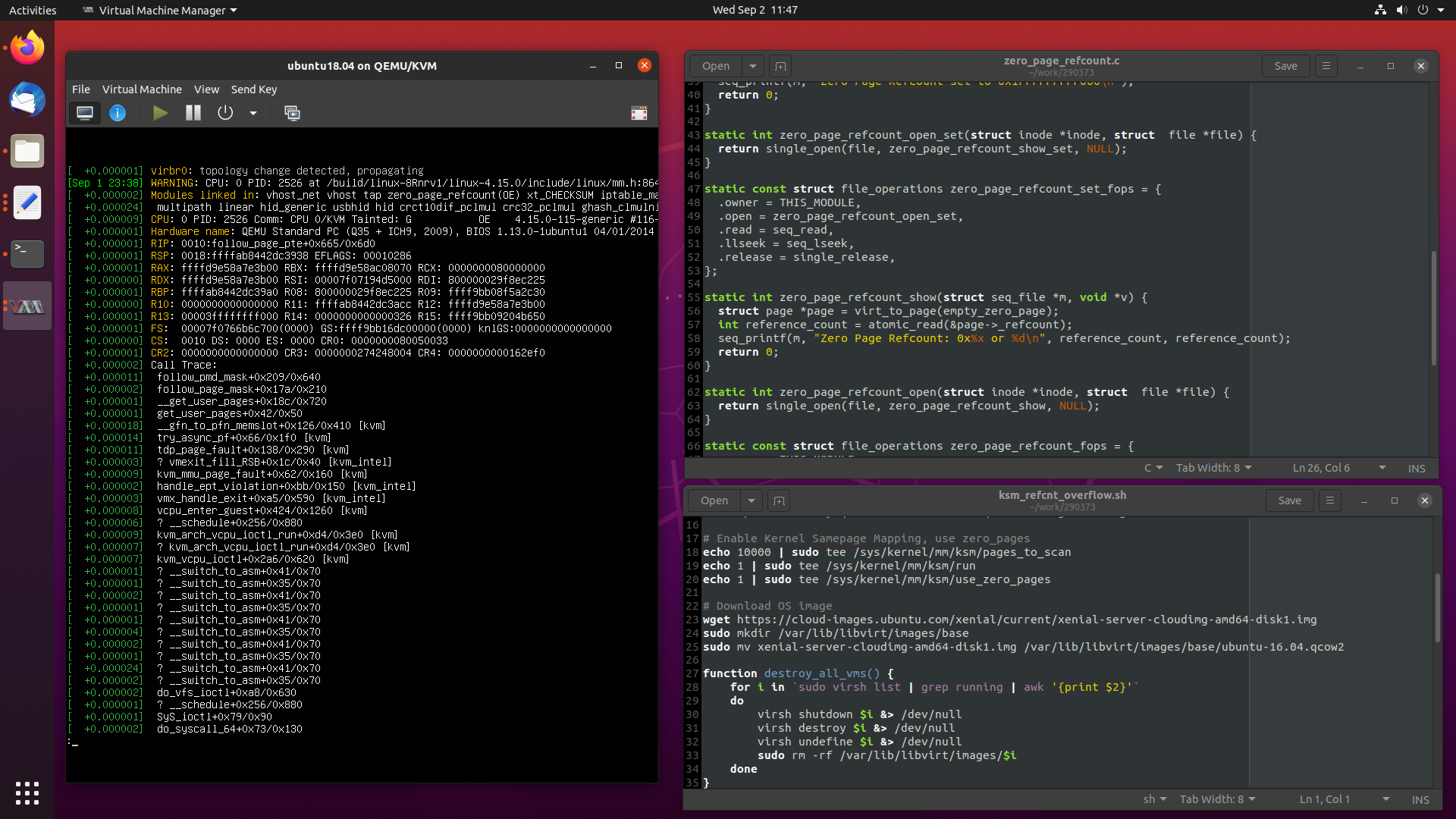
Recently I worked a particularly interesting case where an OpenStack compute node
had all of its virtual machines pause at the same time, which I attributed to
a reference counter overflowing in the kernel’s zero_page.
Today, we are going to take a in-depth look at the problem at hand, and see how
I debugged and fixed the issue, from beginning to completion.
Let’s get started.
More …
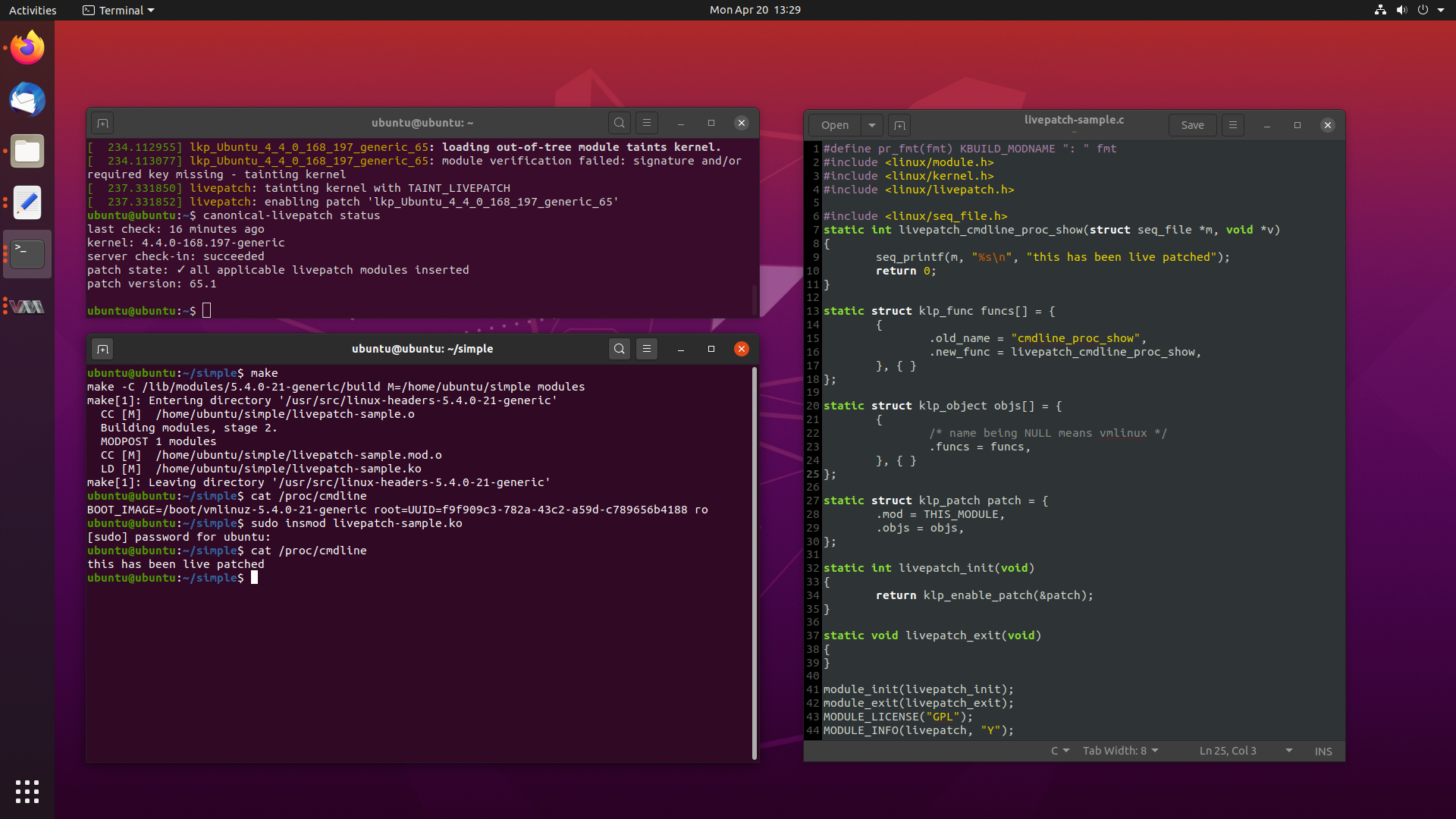
One of the more recent killer features implemented by most major Linux distros
these days is the ability to patch the kernel while it is running, without the
need for a reboot.
While this may sound like sorcery for some, this is a very real feature, called
Livepatch. Livepatch uses ftrace in new and interesting ways, by patching in
calls at the beginning of existing functions to new patched functions, delivered
as kernel modules.
This lets you update and fix bugs on the fly, although its use is typically
reserved for security critical fixes only.
The whole concept is extremely interesting, so today we will look into what
Livepatch is, how it is implemented across several distros, we will write some
Livepatches of our own, and look at how Livepatch works in Ubuntu for end users.
More …
The next article in my series of learning about cloud computing is tackling one
of the larger and more widely used cloud software packages - OpenStack.
OpenStack is a service which lets you provision and manage virtual machines
across a pool of hardware which may have differing specifications and vendors.
Today, we will be deploying a small five node OpenStack cluster in Ubuntu 19.10
Eoan Ermine, so follow along, and let’s get this cluster running.
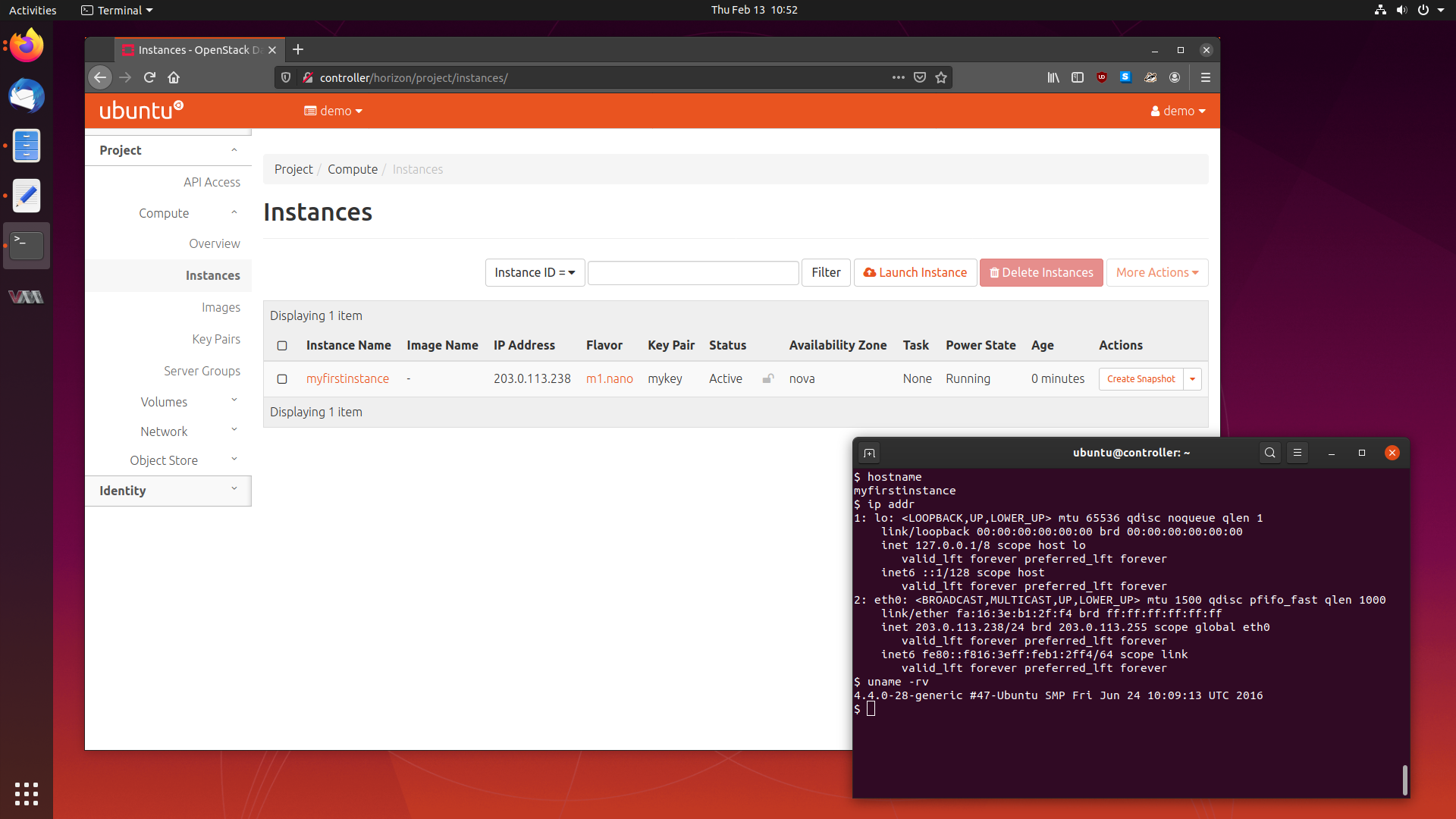
We will cover what OpenStack is, the services it is comprised of, how to deploy
it, and using our cluster to provision some virtual machines.
Let’s get started.
More …
As mentioned previously, I will write about particularly interesting cases I
have worked from start to completion from time to time on this blog.
This is another of those cases. Today, we are going to look at a case where
creating a seemingly innocent RAID array triggers a kernel bug which causes the
system to allocate all of its memory and subsequently crash.
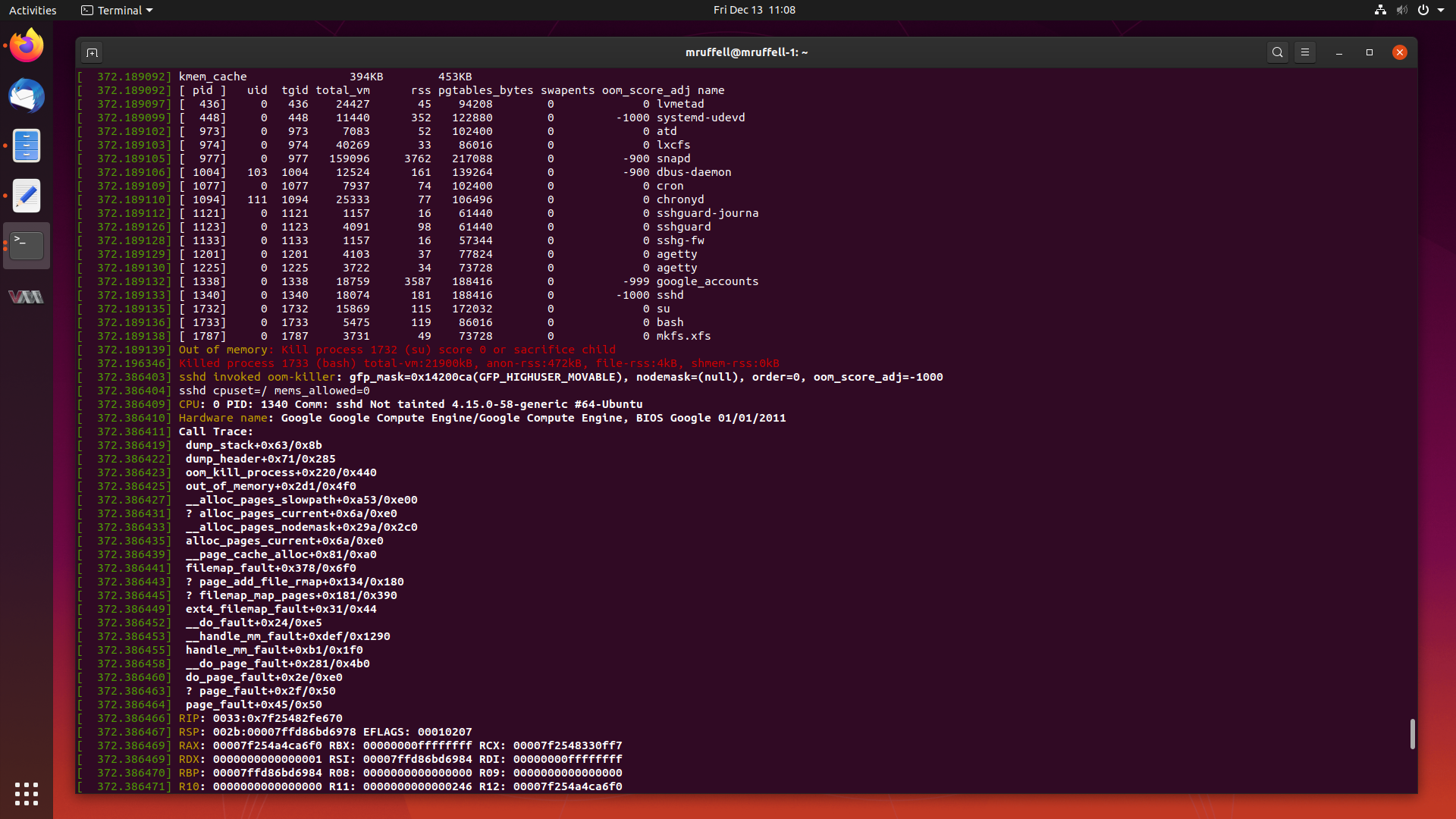
Let’s start digging into this and get this fixed.
More …
In my previous blog post about Juju,
a tool which lets you deploy and scale software easily, we learned what Juju
is, how to deploy some common software packages, debug them, and scale them.
Juju deploys Charms, a set of instructions on how to install, configure and
scale a particular software package. To be able to deploy software as a Charm,
a Charm has to be written first. Usually Charms are written by experts in
operating that software package, so that the Charm represents the best way to
configure and tune that application. But what happens if no Charm exists for
something you want to deploy?
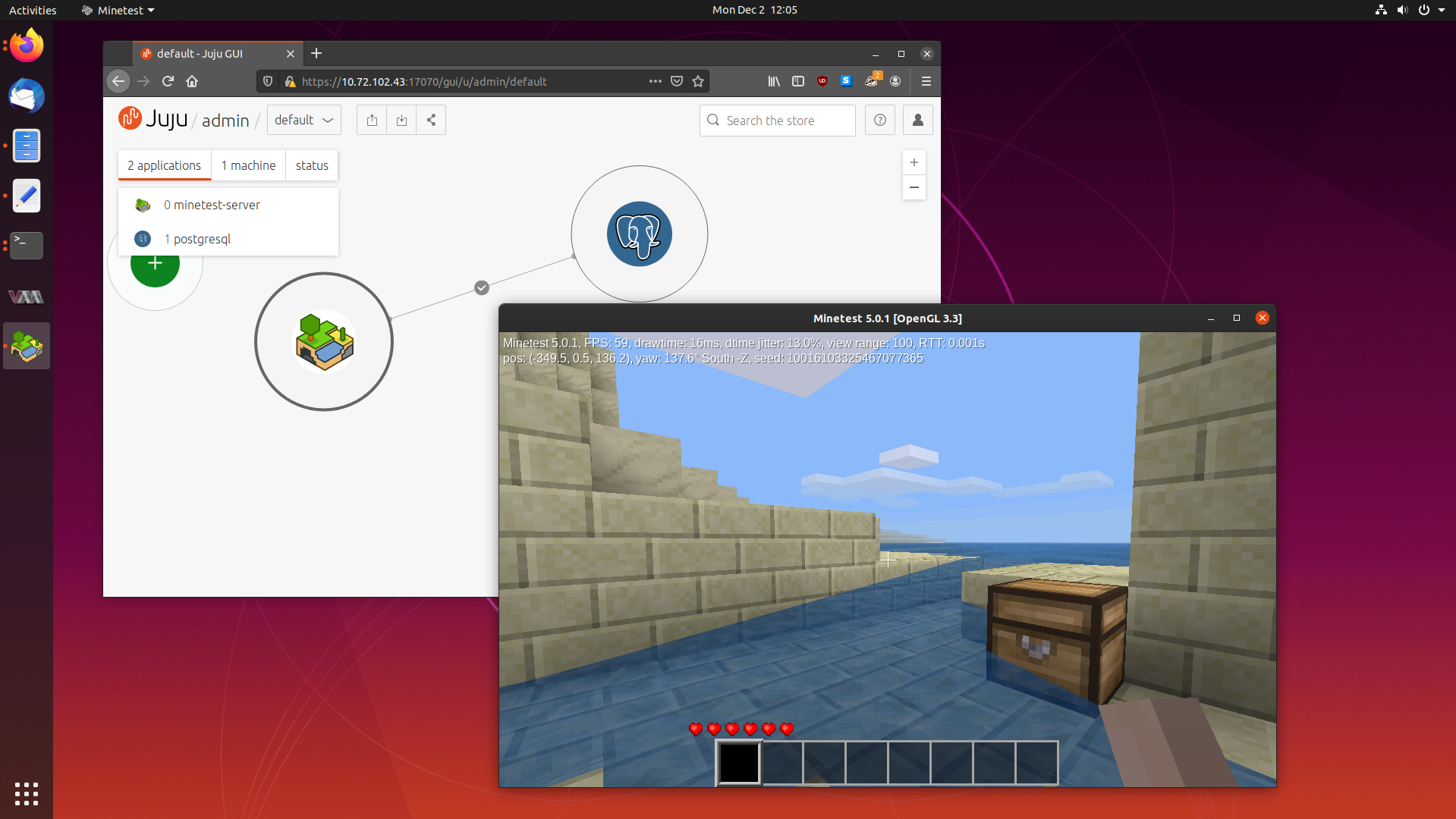
Today we are going to learn how to write our own Charms using the original Charm
writing method, by making a Charm for the Minetest
game server. So fire up your favourite text editor, and lets get started.
More …




