A few months ago when I was applying to the CFP for Chcon, I thought, why not
also submit to Kiwicon / Kawaiicon as well?
My first Kiwicon was in 2012, and I have been going every year since, and I have
always thoroughly enjoyed myself and learnt a lot. I guess it was a bit of a dream
that one day I might be able to present a talk at this super cool conference.
Well, I was pretty ecstatic when I got accepted to speak at Kawaiicon!
Kawaiicon is Kiwicon, but cuter. It actually started off as a joke when the
Kiwicon organisers forgot to renew the kiwicon.org domain name, and brought
kawaiicon.org as a contingency, but I guess this year they followed through and
had a cute themed con!
On Friday morning I gave my talk The Story of the “Uncrackable” Lockbox, and Why
Hackers Need to Work Alongside Developers.
Archive Link.
The talk has been uploaded to Youtube, which you can find below:
You can find a copy of the slides here.
More …
A few months ago, I saw the CFP for Chcon open up, and I thought back to how
much I enjoyed Chcon last year, so I thought why not submit a talk this year.
I wrote up a submission, sent if off and a few weeks later I was delighted to
hear that my talk was accepted! Since then I have been writing, editing and
practising once a day for a fortnight, and I was happy with how things turned out.
On Thursday, I gave my talk The Story of the “Uncrackable” Lockbox, and Why
Hackers Need to Work Alongside Developers,
which is about the series of challenges u/cryptocomicon put forward for testing
the security of his TimeLock software.
The talk has been uploaded to Youtube, which you can find below:
You can find a copy of the slides here.
More …
The next piece of cloud software which has caught my attention is
Juju, a tool which allows you to effortlessly deploy
software to any cloud, and scale it with the touch of a button.
Juju deploys software in the form of Charms, a collection of scripts and
deployment instructions that implements industry best practices and knowledge
about that particular software package.
Today we are going to take a deep dive into Juju, and explore how it works,
how to set it up and how to deploy and scale some common software.
More …
Have you ever wondered what a day in the life of a Sustaining Engineer at
Canonical looks like?
Well today, we are going to have a look into a particularly interesting case I
worked from start to completion, as it demanded that I dive into the world of
Linux performance analysis tools to track down and solve the problem.
The problem is that there is a large performance degradation when reading files
from a mounted read-only LVM snapshot on the Ubuntu 4.4 kernel, when compared
to reading from a standard LVM volume. Reads can take anywhere from 14-25x the
amount of time, which is a serious problem.
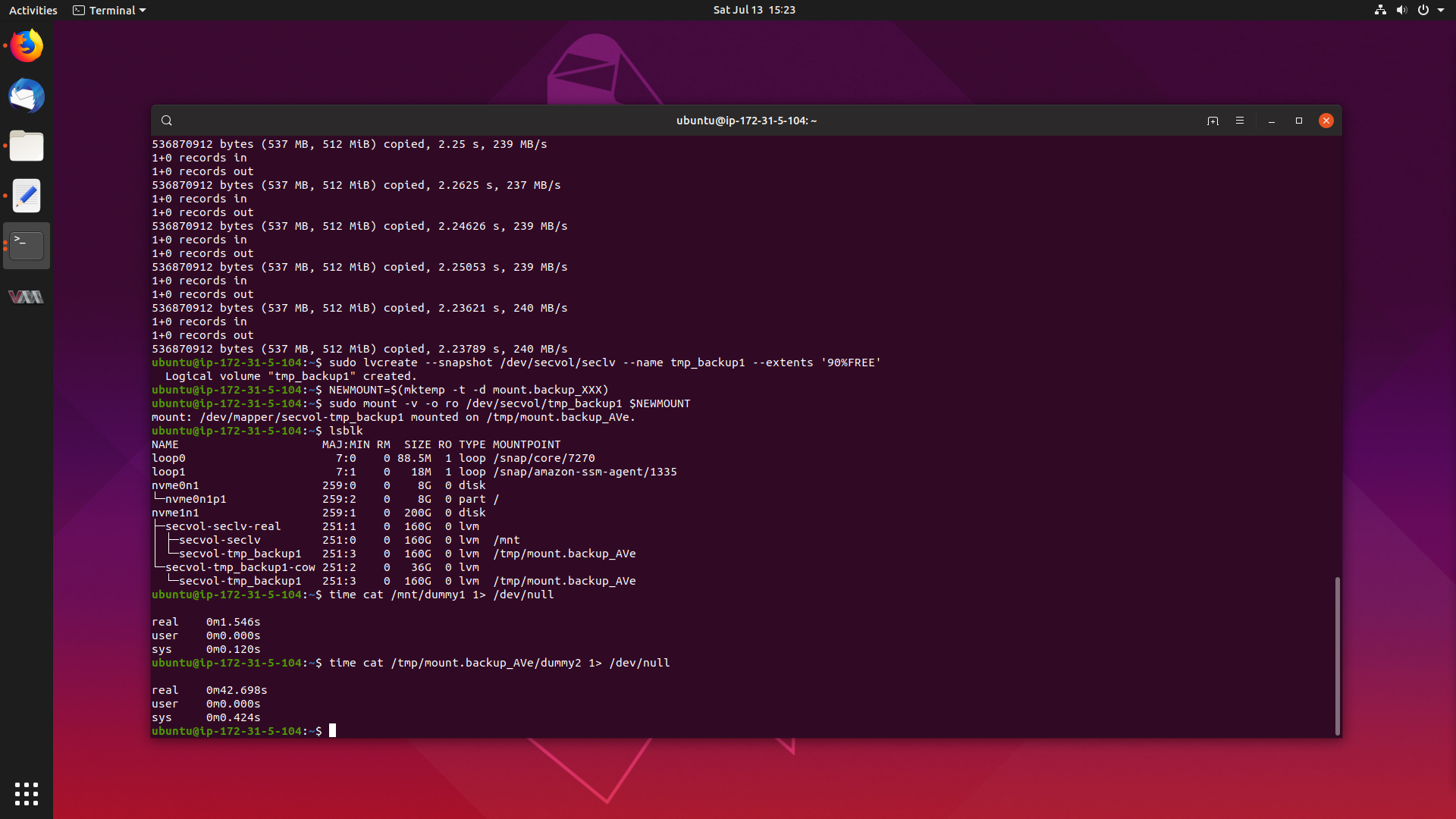
Lets get to the bottom of this, and get this fixed.
More …
A few months ago I made one of the largest decisions in my life - to leave my
PhD position at the University of Canterbury and go out into the world and get
a job.
I am wonderfully excited to announce that I am now a Sustaining Engineer at
Canonical, the company which sponsors
Ubuntu Linux.

I started on the 11th of March 2019, and the last four months I have settled
into my role nicely.
More …


